We Don’t Trust Devices, Neither Should You
Zero Device Trust
(Most of) the devices accessing your services are safe. Right?
You trust your tall stack of endpoint tools
From MDM to EDR to different patching tools - and you've even got ZTNA, SSE, and 15 other acronyms. It should be enough, right?
You’ve set great security policies
Users eagerly anticipate the latest security patches and immediately relaunch their apps or reboot their computers, don’t they?
You have a killer IT Ops team
They storm in for every critical vulnerability, sending alerts to everyone and swiftly deploying patches. But can they really reach every device in your org in time?
It only takes one unpatched device
for an attacker to gain access to your resources
Why is it so hard to get
every single device inline?
The sheer scope of devices and weak posture issues are overwhelming
Thousands of devices, weak operating system configurations, missing security agents and pending critical updates make your head spin.
Thousands of devices, weak operating system configurations, missing security agents and pending critical updates make your head spin.
Existing tools are not designed to verify device updates on-access
Applying critical updates regularly is important, but it works in another timeline regardless of granting access to your sensitive data and services. Over time, all your devices have been given uncontrolled access to resources while they were critically vulnerable.
Applying critical updates regularly is important, but it works in another timeline regardless of granting access to your sensitive data and services. Over time, all your devices have been given uncontrolled access to resources while they were critically vulnerable.
Blocking users without
a solution and harming productivity is not an option
Although blocking vulnerable devices from accessing your resources sounds obvious, but it just not gonna fly with your users as work needs to keep flowing. (and your IT help-desk won’t appreciate that as well...)
Although blocking vulnerable devices from accessing your resources sounds obvious, but it just not gonna fly with your users as work needs to keep flowing. (and your IT help-desk won’t appreciate that as well...)
Get all your devices in line, all the time,
with Infinipoint's Zero Device Trust.
Set and enforce granular security and compliance policies
Follow best practices or set your own policies to run any update, any check, and any control for any user -- or user group. So you can cover hundreds of compliance verifications, OS configurations, 3rd party app critical updates, and more.
Follow best practices or set your own policies to run any update, any check, and any control for any user -- or user group. So you can cover hundreds of compliance verifications, OS configurations, 3rd party app critical updates, and more.
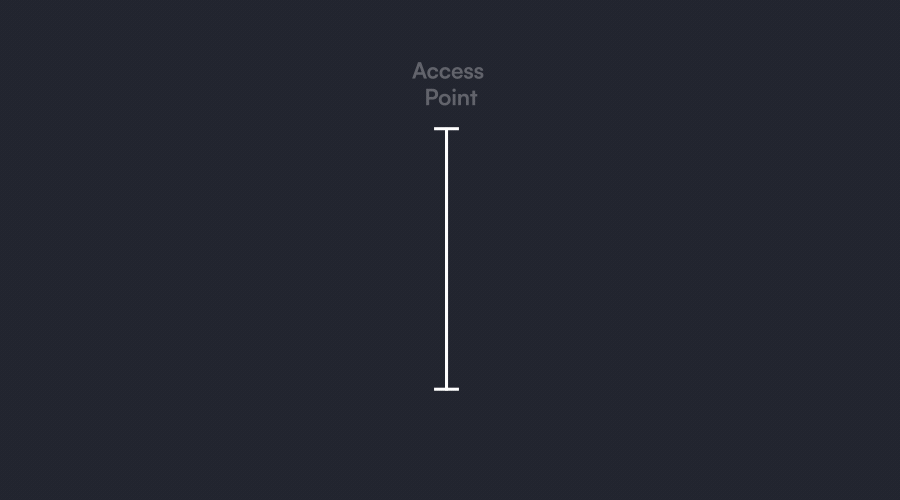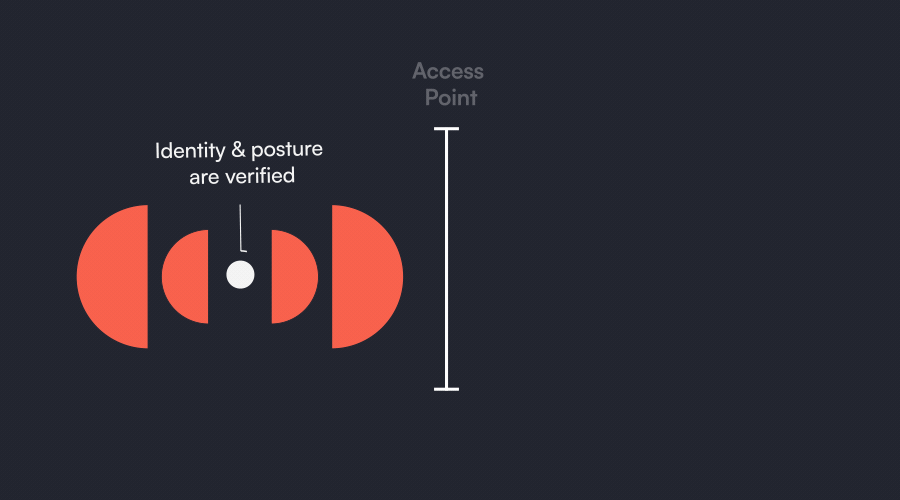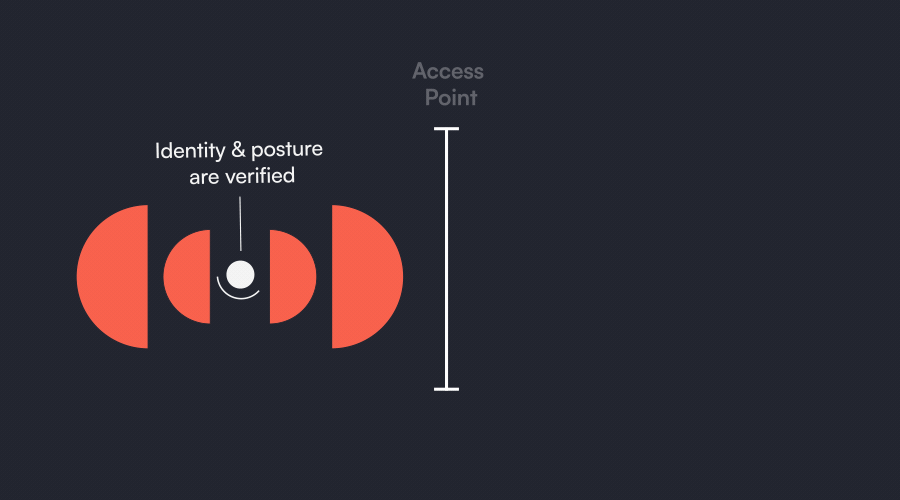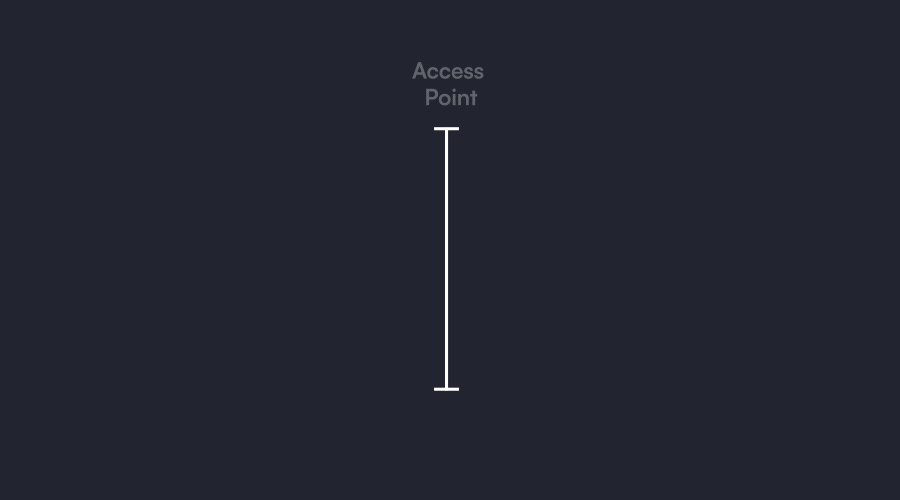
Automatic
Posture Verification
On-access
Verify critical device posture when it matters: at the point of access, and continuously.. Ensure only secured devices will be granted access to your systems.
Verify critical device posture when it matters: at the point of access, and continuously.. Ensure only secured devices will be granted access to your systems.
Remediate vulnerabilities
in a single click
Define real-time remediation scenarios and set grace periods upfront so users can remediate in a snap and continue working, uninterrupted.
Define real-time remediation scenarios and set grace periods upfront so users can remediate in a snap and continue working, uninterrupted.
